Types of cyber security threats
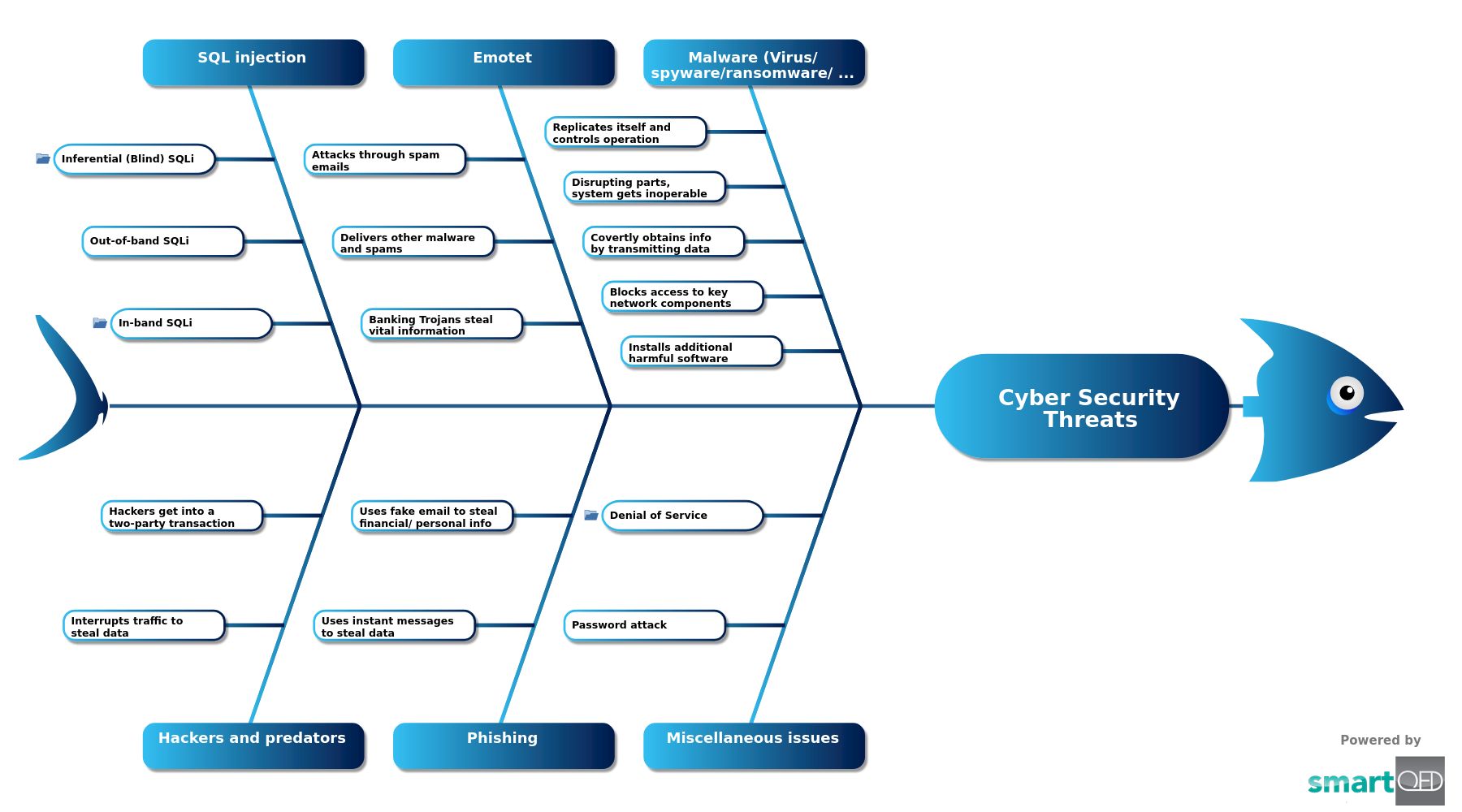
Cyber security threat or breach is a malicious attack to achieve unauthorized access then damage and steal digital assets, computer networks, or any sensitive data. The attack may be intended to disrupt digital operations too. The sources of such threats could be corporate spies, hacktivists, terrorist groups, criminal organizations, hostile nation-states or revengeful employees. Some cyber hackers’ aim is to gain financial benefits. They bring down a system and demand money to restore the functionality. For example, ransomware is a sophisticated cyber-attack that claims money to reinstate the service. Corporate businesses, individuals as well as national defense departments are vulnerable to cyber threats. Failure to implement, test and retest technical safeguards, such as encryption, authentication and firewalls weaken the security system. Tracking down the attacks and attackers is the key to strong cyber security. Cyber security professionals’ job is to develop sound knowledge of threats and their origins.
Cyber Security Threats
Malware (Virus/ spyware/ransomware/ worm)
Miscellaneous issues
Emotet
Phishing
SQL injection
Hackers and predators
This fishbone analyzes some of the major ways of cyber security attacks. This template helps everyone to organize the reasons for any such issue. We have created several categories based on the nature of the attacks. The depth goes on increasing as we find and add new items to their higher-level parent group.
Curated from community experience and public sources: